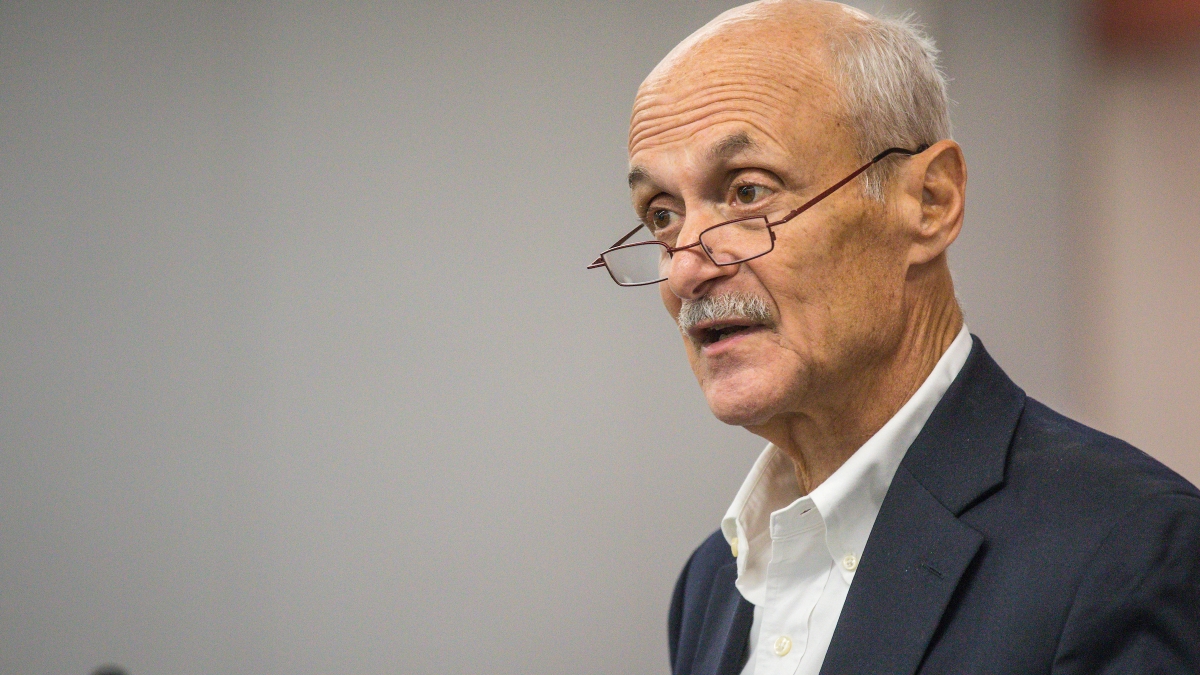Cybersecurity infiltrations and terrorist attacks have filled the headlines in recent months. These issues pose a significant threat to U.S. national security and are likely to increase in the coming decade. Current efforts to protect against these threats can increase vulnerabilities and lead to invasions of privacy.
How much of our privacy must be sacrificed to achieve real security?
Former U.S. Secretary of Homeland Security Michael Chertoff and leaders from industry and academia met in an open forum Monday at Arizona State University to discuss this topic. The event, “Unlocking the Privacy-Security Debate,” was hosted jointly by the Sandra Day O’Connor College of Law and the Global Security Initiative at the Beus Center for Law and Society.
To Chertoff (pictured above), the goals of privacy and security are not mutually exclusive.
“I think security and privacy are not only better together, I think they have to be together,” he said. “They are two sides of the same coin.”
Cybersecurity breaches are in the news nearly every day, and the discussion tends to confuse these concepts by treating privacy and security as a zero-sum game, Chertoff said.
“All of this warrants a cool appraisal of where we are and where we need to be.”
Chertoff served as the second secretary of the U.S. Department of Homeland Security from 2005 to 2009. Previously, he worked as a federal judge on the U.S. Court of Appeals for the Third Circuit. Today, he is chairman and co-founder of the Chertoff Group, providing strategic counsel on global security solutions.
Chertoff took a measured view on government surveillance at the ASU forum, allowing that the intelligence community has a responsibility to disclose vulnerabilities that affect the general public, even if they may be exploited against our enemies. However, when it comes to metadata — the equivalent of telephone records — the secretary took a much more nuanced view.
“Surveillance should be viewed as a continuum,” he said Monday, making a distinction between the different phases of the intelligence process: collection, inspection, analysis and dissemination. According to Chertoff, often with metadata the significance is only evident in hindsight, and if that data has been collected and stored, it can be referenced to connect individual terrorists within networks.
Although when thinking about privacy we tend to picture government surveillance, “it’s amazing how much of our personal data is out there, not just from the government but the private sector — the volume is growing exponentially,” Chertoff said.
He also touched on other concerns that arise in our technologically enabled modern world. For instance, we may enjoy a discount from our health insurance provider when we share data from a fitness tracker. However, Chertoff warned that discounts for one person could mean penalties for another, and a future where we have “Big Mother” making sure we get enough exercise and eat our vegetables is far from unimaginable. This describes a violation of autonomy, our ability to make decisions freely, he said.
Privacy violations can be even more immediately dire when Wi-Fi-enabled pacemakers and self-driving cars are considered. These types of devices make up the Internet of Things, which could more aptly be called the “Internet of Everything,” according to Michelle Dennedy, vice president and chief privacy officer of tech conglomerate Cisco who also spoke at the event.
What can be done? How to do we solve this complex problem?
According to Ann Cavoukian, executive director of the Privacy and Big Data Institute at Ryerson University, we need to go back to square one. Privacy should be the default setting, embedded into the design. “Reject the notion that you are in the post-privacy era,” she insisted.
Jamie Winterton, director of Strategic Research Initiatives at GSI, echoed this solution, saying, “You don’t have to sacrifice your privacy to be secure.” Winterton suggested working with tech experts from the university as well as strategic partners to create technologies that preserve privacy, but not at the expense of security.
Ultimately, however, we are all responsible for our own individual privacy and security.
“It’s not a government function to protect you — you have to protect yourselves,” Chertoff said.
To watch Chertoff's entire talk, click here.
Top photo: Former Secretary of Homeland Security Michael Chertoff speaks Monday at the "Unlocking the Privacy-Security Debate" event at the Beus Center for Law and Society on ASU's Downtown Phoenix campus. He discussed a nuanced approach for both privacy and security, with privacy paramount, but the need to access metadata to draw possible connections to prevent terrorist acts. Photo by Charlie Leight/ASU Now
More Law, journalism and politics

Annual John P. Frank Memorial Lecture enters its 26th year
Dahlia Lithwick, an MSNBC analyst and senior legal correspondent at Slate, is the featured speaker at the School of Social Transformation’s 26th annual John P. Frank Memorial Lecture on…

The politics behind picking a romantic partner
A new study reveals the role that politics play when picking out a romantic partner — particularly for older adults.“Findings show that politics are highly salient in partner selection across gender…

Tips to make tax season less taxing
When it comes to highly unpleasant experiences, filing taxes is probably up there with root canals — which is why people put off doing them. But tax season is here, and in an effort to alleviate…