Married to the military

Military spouses often face situations and challenges that most civilians don’t — deployments, long periods of separation and adhering to codes that sometimes can stifle human emotion.
But with adaptability, dependability and a good set of ears, those issues often can get worked out, said one Arizona State University military spouse.
“There’s many challenges that I was not prepared for and that we were not aware of,” said Army veteran and ASU alumna Karen Cruz, who is married to Melvin Cruz, also an Army veteran and ASU graduate. “But we learned along the way.”
Many such lessons were learned and exchanged in a May 11 Zoom webinar titled “Veteran Voices: The Spouse Experience in the Military and in Higher Education,” hosted by ASU’s Pat Tillman Veterans Center.
To celebrate Military Spouse Appreciation Day, the center hosted a panel of ASU staff, students and alumni who shared their experiences about serving in the military and continuing their service at ASU.
“Our student veterans at ASU come from diverse backgrounds, just like the fabric of American society. The experiences and perspectives they bring are valuable, so we built a platform for them to share through Veteran Voices,” said Jeff Guimarin, director of the Tillman Center. “This helps build a stronger, more inclusive community across ASU and enables us to bring the civilian and military gap of understanding closer together.”
He said the ultimate hope of the Veteran Voices series is to spark dialogue and awareness that will lead to positive action.
The Tillman Center created the Veteran Voices series to align with the 25 initiatives ASU President Michael Crow put into place in 2020 to contribute to a national agenda for social justice after the murder of George Floyd and a wave of Black Lives Matter protests. The first installment, “Veteran Voices: The Black Experience in the Military and in Higher Education,” was a way to have an engaging dialogue on the topics of the Black Lives Matter movement and being Black in the military. From there, the Tillman Center realized there were more groups that needed to be heard.
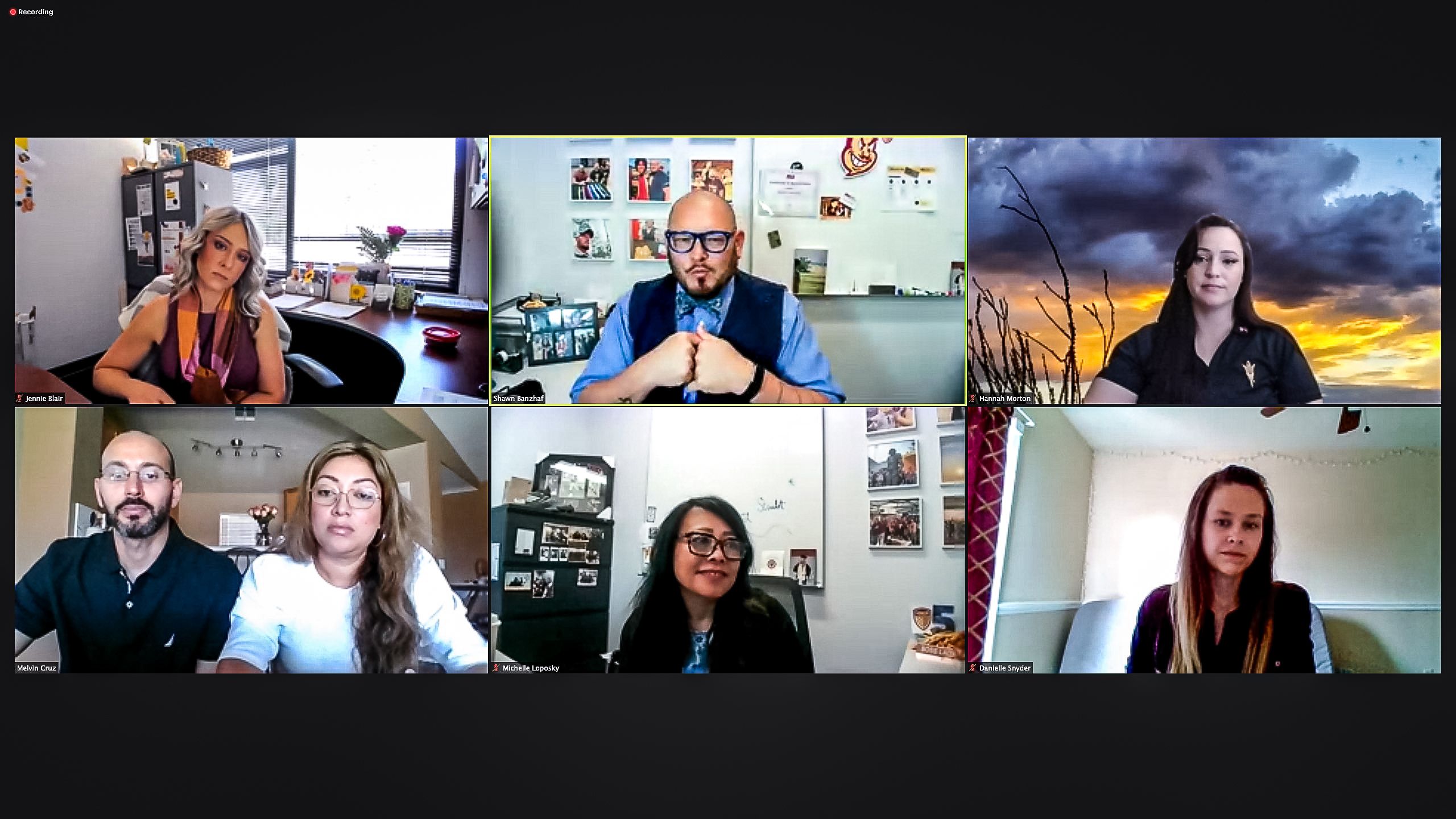
In addition to Karen and Melvin Cruz, the panel included Jennie Blair, assistant director for University Registrar Services at the Downtown Phoenix campus and the spouse of an Navy and Army veteran, and Hannah Morton, a Marine Corps spouse. Moderating duties were handled by Shawn Banzhaf, Michelle Loposky and Danielle Snyder, all with the Tillman Center.
Military spouses Jennie Blair (top left), Hannah Morton (top right) and Melvin and Karen Cruz (lower left) participate in a webcast panel discussion for the Pat Tillman Veterans Center’s “Veteran Voices: The Spouse Experience in the Military and in Higher Education” on May 11. The Tillman Center’s Shawn Banzhaf (top center) moderated the discussion with the assistance of Michelle Loposky (bottom center) and Danielle Snyder. The panel discussion ranged from surviving deployments to supporting their spouses during the transition to being civilians. Photo by Charlie Leight/ASU News
The discussion lit on personal stories about deployments, the caregiver role, personal space, sharing sensitive information, the military/veteran family culture and the adoption of civilian life.
For Morton, life in the military certainly had more upsides than downsides.
“I think it’s made me stronger, and I adapt better to life. I don’t think I could have handled things as well as I had in the past,” said Morton, a current ASU Online student working toward her bachelor's degree in sports business from the W. P. Carey School of Business and a minor in communication from The College of Liberal Arts and Sciences. “I bought a house basically by myself, I’ve gone through multiple deployments and I’ve traveled across the ocean and back. I’m actually thankful it’s made me better, stronger and more knowledgeable.”
Melvin Cruz, who saw combat in Iraq, said being married to a fellow veteran has deepened the bonds of their marriage because there’s an inherent understanding of military life.
“Our connection became deep really fast because of our circumstances,” said Cruz, who graduated in December 2020 with a bachelor’s degree in public service and public policy. “I do know for sure that if I were married to a civilian, I would probably be divorced by now.”
Blair said being married to a veteran requires a delicate balancing act. She said it is wise to find a support system, especially during a deployment.
“When (Jack) was in Afghanistan, there was a time when he hit a super low point, and I was at my limit in terms of how I could help him,” said Blair, who received a bachelor’s degree in English from ASU in May 2001. “So it’s also about, ‘Do you have a community or buddy you can reach out to and ask for help when you’ve reached your limit?’”
The panel was also asked to share some of their favorite memories of the military. The answer came easily to Morton.
“Our favorite installation was Kaneohe, Hawaii. It was just a walk from the beach and the dog park,” said Morton, who is a student worker at the Tillman Center. “You would see families taking walks there and it was such a family-oriented place. It was smaller and everyone was closer.”
Whatever hardships were endured while in the military, Karen Cruz said the experiences and the friendships they forged was all worth it in the end.
“Nobody misses marching, 10-mile runs or being woken up at 3 in the morning to do nothing, but I do miss the friendships that you form in your group,” Cruz said. “I miss those moments.”
Top photo courtesy of iStock/Getty Images